Merge pull request #64 from mjanez/ckan-master
Update ckan 08/23: Sol4 9, Security options and other fixes
This commit is contained in:
commit
6d52733a5e
29
.env.example
29
.env.example
|
|
@ -13,13 +13,13 @@ PYCSW_CONTAINER_NAME=pycsw
|
||||||
|
|
||||||
# Host Ports
|
# Host Ports
|
||||||
CKAN_PORT_HOST=5000
|
CKAN_PORT_HOST=5000
|
||||||
NGINX_PORT_HOST=80
|
NGINX_PORT_HOST=81
|
||||||
NGINX_SSLPORT_HOST=8443
|
NGINX_SSLPORT_HOST=8443
|
||||||
APACHE_PORT_HOST=80
|
APACHE_PORT_HOST=81
|
||||||
PYCSW_PORT_HOST=8000
|
PYCSW_PORT_HOST=8000
|
||||||
|
|
||||||
# Solr
|
# Solr
|
||||||
SOLR_IMAGE_VERSION=2.9-solr8-spatial
|
SOLR_IMAGE_VERSION=2.9-solr9-spatial
|
||||||
SOLR_PORT=8983
|
SOLR_PORT=8983
|
||||||
CKAN_SOLR_URL=http://solr:${SOLR_PORT}/solr/ckan
|
CKAN_SOLR_URL=http://solr:${SOLR_PORT}/solr/ckan
|
||||||
TEST_CKAN_SOLR_URL=http://solr:${SOLR_PORT}/solr/ckan
|
TEST_CKAN_SOLR_URL=http://solr:${SOLR_PORT}/solr/ckan
|
||||||
|
|
@ -47,8 +47,8 @@ PROXY_PYCSW_LOCATION=/csw
|
||||||
|
|
||||||
# pycsw
|
# pycsw
|
||||||
PYCSW_PORT=8000
|
PYCSW_PORT=8000
|
||||||
CKAN_URL=http://localhost/catalog
|
CKAN_URL=https://localhost:8443/catalog
|
||||||
PYCSW_URL=http://localhost/csw
|
PYCSW_URL=https://localhost:8443/csw
|
||||||
# SCHEMAS: ckan2pycsw/model/dataset.py - Dataset type
|
# SCHEMAS: ckan2pycsw/model/dataset.py - Dataset type
|
||||||
PYCSW_CKAN_SCHEMA=iso19139_geodcatap
|
PYCSW_CKAN_SCHEMA=iso19139_geodcatap
|
||||||
PYCSW_OUPUT_SCHEMA=iso19139_inspire
|
PYCSW_OUPUT_SCHEMA=iso19139_inspire
|
||||||
|
|
@ -61,13 +61,18 @@ PYCSW_CRON_HOUR_START=4
|
||||||
TZ=UTC
|
TZ=UTC
|
||||||
|
|
||||||
# CKAN databases
|
# CKAN databases
|
||||||
POSTGRES_USER=ckan
|
POSTGRES_USER=postgres
|
||||||
POSTGRES_PASSWORD=ckan
|
POSTGRES_PASSWORD=postgres
|
||||||
|
POSTGRES_DB=postgres
|
||||||
|
POSTGRES_HOST=db
|
||||||
|
CKAN_DB_USER=ckandbuser
|
||||||
|
CKAN_DB_PASSWORD=ckandbpassword
|
||||||
|
CKAN_DB=ckandb
|
||||||
DATASTORE_READONLY_USER=datastore_ro
|
DATASTORE_READONLY_USER=datastore_ro
|
||||||
DATASTORE_READONLY_PASSWORD=datastore
|
DATASTORE_READONLY_PASSWORD=datastore
|
||||||
POSTGRES_HOST=db
|
DATASTORE_DB=datastore
|
||||||
CKAN_SQLALCHEMY_URL=postgresql://ckan:ckan@db/ckan
|
CKAN_SQLALCHEMY_URL=postgresql://ckandbuser:ckandbpassword@db/ckandb
|
||||||
CKAN_DATASTORE_WRITE_URL=postgresql://ckan:ckan@db/datastore
|
CKAN_DATASTORE_WRITE_URL=postgresql://ckandbuser:ckandbpassword@db/datastore
|
||||||
CKAN_DATASTORE_READ_URL=postgresql://datastore_ro:datastore@db/datastore
|
CKAN_DATASTORE_READ_URL=postgresql://datastore_ro:datastore@db/datastore
|
||||||
|
|
||||||
# Test database connections
|
# Test database connections
|
||||||
|
|
@ -80,7 +85,7 @@ TEST_CKAN_DATASTORE_READ_URL=postgresql://datastore_ro:datastore@db/datastore_te
|
||||||
CKAN_VERSION=2.9.9
|
CKAN_VERSION=2.9.9
|
||||||
CKAN_SITE_ID=default
|
CKAN_SITE_ID=default
|
||||||
# CKAN_SITE_URL = http:/ or https:/ + PROXY_SERVER_NAME. Optionally the APACHE_HOST_PORT if different from 80
|
# CKAN_SITE_URL = http:/ or https:/ + PROXY_SERVER_NAME. Optionally the APACHE_HOST_PORT if different from 80
|
||||||
CKAN_SITE_URL=http://localhost
|
CKAN_SITE_URL=https://localhost:8443
|
||||||
CKAN__ROOT_PATH=/catalog/{{LANG}}
|
CKAN__ROOT_PATH=/catalog/{{LANG}}
|
||||||
CKAN_PORT=5000
|
CKAN_PORT=5000
|
||||||
CKAN__FAVICON=/catalog/base/images/ckan.ico
|
CKAN__FAVICON=/catalog/base/images/ckan.ico
|
||||||
|
|
@ -131,7 +136,7 @@ CKANEXT__XLOADER__API_TOKEN=api_token
|
||||||
CKANEXT__XLOADER__JOBS__DB_URI=postgresql://ckan:ckan@db/ckan
|
CKANEXT__XLOADER__JOBS__DB_URI=postgresql://ckan:ckan@db/ckan
|
||||||
|
|
||||||
# ckanext-dcat
|
# ckanext-dcat
|
||||||
CKANEXT__DCAT__BASE_URI=http://localhost/catalog
|
CKANEXT__DCAT__BASE_URI=https://localhost:8443/catalog
|
||||||
CKANEXT__DCAT__RDF_PROFILES="euro_dcat_ap_2 euro_dcat_ap"
|
CKANEXT__DCAT__RDF_PROFILES="euro_dcat_ap_2 euro_dcat_ap"
|
||||||
|
|
||||||
# ckanext-spatial (Solr Backend - solr8-spatial)
|
# ckanext-spatial (Solr Backend - solr8-spatial)
|
||||||
|
|
|
||||||
68
README.md
68
README.md
|
|
@ -101,6 +101,7 @@ versions for client and server.
|
||||||
> Learn more about [Docker](#docker-basic-commands)/[Docker Compose](#docker-compose-basic-commands) basic commands.
|
> Learn more about [Docker](#docker-basic-commands)/[Docker Compose](#docker-compose-basic-commands) basic commands.
|
||||||
>
|
>
|
||||||
|
|
||||||
|
|
||||||
## Install (build and run) CKAN plus dependencies
|
## Install (build and run) CKAN plus dependencies
|
||||||
### Base mode
|
### Base mode
|
||||||
Use this if you are a maintainer and will not be making code changes to CKAN or to CKAN extensions.
|
Use this if you are a maintainer and will not be making code changes to CKAN or to CKAN extensions.
|
||||||
|
|
@ -168,6 +169,7 @@ After this step, CKAN should be running at {`PROXY_SERVER_NAME`}{`PROXY_CKAN_LOC
|
||||||
|2cdd25cea0de|ckan-docker-db |docker-entrypoint.s…|6 minutes ago |Up 4 minutes (healthy)|5432/tcp |db | |
|
|2cdd25cea0de|ckan-docker-db |docker-entrypoint.s…|6 minutes ago |Up 4 minutes (healthy)|5432/tcp |db | |
|
||||||
|9cdj25dae6gr|ckan-docker-pycsw |docker-entrypoint.s…|6 minutes ago |Up 4 minutes (healthy)|8000/tcp |pycsw | |
|
|9cdj25dae6gr|ckan-docker-pycsw |docker-entrypoint.s…|6 minutes ago |Up 4 minutes (healthy)|8000/tcp |pycsw | |
|
||||||
|
|
||||||
|
|
||||||
### Quick mode
|
### Quick mode
|
||||||
If you just want to test the package and see the general functionality of the platform, you can use the `ckan-spatial` image from the [Github container registry](https://github.com/mjanez/ckan-docker/pkgs/container/ckan-spatial):
|
If you just want to test the package and see the general functionality of the platform, you can use the `ckan-spatial` image from the [Github container registry](https://github.com/mjanez/ckan-docker/pkgs/container/ckan-spatial):
|
||||||
|
|
||||||
|
|
@ -179,6 +181,7 @@ If you just want to test the package and see the general functionality of the pl
|
||||||
|
|
||||||
It will download the pre-built image and deploy all the containers. Remember to use your own domain by changing `localhost` in the `.env` file.
|
It will download the pre-built image and deploy all the containers. Remember to use your own domain by changing `localhost` in the `.env` file.
|
||||||
|
|
||||||
|
|
||||||
### Development mode
|
### Development mode
|
||||||
Use this mode if you are making code changes to CKAN and either creating new extensions or making code changes to existing extensions. This mode also uses the `.env` file for config options.
|
Use this mode if you are making code changes to CKAN and either creating new extensions or making code changes to existing extensions. This mode also uses the `.env` file for config options.
|
||||||
|
|
||||||
|
|
@ -238,7 +241,6 @@ The Docker image config files used to build your CKAN project are located in the
|
||||||
>```
|
>```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
## CKAN images enhancement
|
## CKAN images enhancement
|
||||||
### Extending the base images
|
### Extending the base images
|
||||||
You can modify the docker files to build your own customized image tailored to your project, installing any extensions and extra requirements needed. For example here is where you would update to use a different CKAN base image ie: `ckan/ckan-base-spatial:<new version>`
|
You can modify the docker files to build your own customized image tailored to your project, installing any extensions and extra requirements needed. For example here is where you would update to use a different CKAN base image ie: `ckan/ckan-base-spatial:<new version>`
|
||||||
|
|
@ -310,7 +312,8 @@ ckan
|
||||||
|
|
||||||
|
|
||||||
## ckan-docker addons
|
## ckan-docker addons
|
||||||
### VSCode dev containers
|
### Debugging
|
||||||
|
#### VSCode dev containers
|
||||||
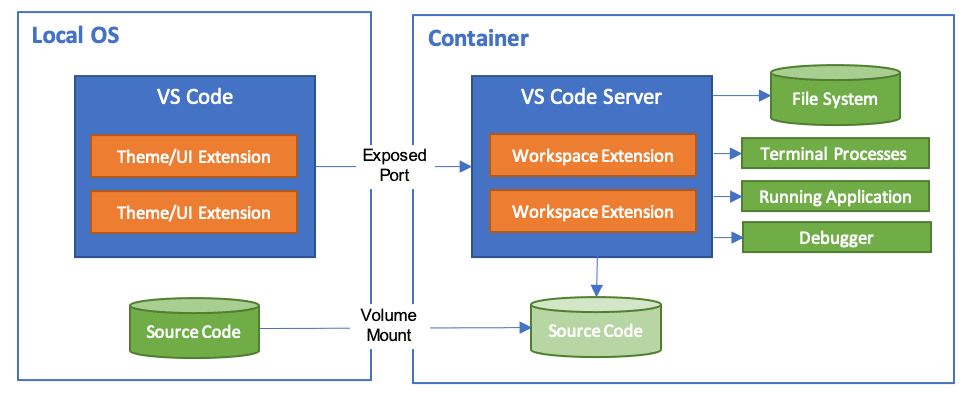
The [Visual Studio Code Dev Containers](https://code.visualstudio.com/docs/devcontainers/containers) extension is a powerful tool that enables developers to use a container as a complete development environment. With this extension, developers can open any folder inside a container and take advantage of the full range of features provided by Visual Studio Code. To do this, developers create a `devcontainer.json `file in their project that specifies how to access or create a development container with a predefined tool and runtime stack. This allows developers to work in an isolated environment, ensuring that the development environment is consistent across team members and that project dependencies are easy to manage.
|
The [Visual Studio Code Dev Containers](https://code.visualstudio.com/docs/devcontainers/containers) extension is a powerful tool that enables developers to use a container as a complete development environment. With this extension, developers can open any folder inside a container and take advantage of the full range of features provided by Visual Studio Code. To do this, developers create a `devcontainer.json `file in their project that specifies how to access or create a development container with a predefined tool and runtime stack. This allows developers to work in an isolated environment, ensuring that the development environment is consistent across team members and that project dependencies are easy to manage.
|
||||||
|
|
||||||
|

|
||||||
|
|
@ -330,7 +333,7 @@ The [Visual Studio Code Dev Containers](https://code.visualstudio.com/docs/devco
|
||||||
7. VSCode will start a new container based on the configuration settings in your `devcontainer.json` file. Once the container is started, you can work on your project just like you would on your local machine.
|
7. VSCode will start a new container based on the configuration settings in your `devcontainer.json` file. Once the container is started, you can work on your project just like you would on your local machine.
|
||||||
|
|
||||||
|
|
||||||
### pdb
|
#### pdb
|
||||||
Add these lines to the `ckan-dev` service in the docker compose.dev.yml file
|
Add these lines to the `ckan-dev` service in the docker compose.dev.yml file
|
||||||
|
|
||||||

|

|
||||||
|
|
@ -340,11 +343,8 @@ Debug with pdb (example) - Interact with `docker attach $(docker container ls -q
|
||||||
command: `python -m pdb /usr/lib/ckan/venv/bin/ckan --config /srv/app/ckan.ini run --host 0.0.0.0 --passthrough-errors`
|
command: `python -m pdb /usr/lib/ckan/venv/bin/ckan --config /srv/app/ckan.ini run --host 0.0.0.0 --passthrough-errors`
|
||||||
|
|
||||||
|
|
||||||
### Datastore
|
### Reverse proxy
|
||||||
The Datastore database and user is created as part of the entrypoint scripts for the db container.
|
#### NGINX
|
||||||
|
|
||||||
|
|
||||||
### NGINX
|
|
||||||
The default Docker Compose configuration ([`docker-compose.yml`](/docker-compose.yml)) uses an NGINX image as the front-end (ie: reverse proxy). It includes HTTPS running on port number 8443 and an HTTP port (81). A "self-signed" SSL certificate is generated beforehand and the server certificate and key files are included. The NGINX `server_name` (ENV: `PROXY_SERVER_NAME`) directive and the `CN` field in the SSL certificate have been both set to 'localhost'. This should obviously not be used for production.
|
The default Docker Compose configuration ([`docker-compose.yml`](/docker-compose.yml)) uses an NGINX image as the front-end (ie: reverse proxy). It includes HTTPS running on port number 8443 and an HTTP port (81). A "self-signed" SSL certificate is generated beforehand and the server certificate and key files are included. The NGINX `server_name` (ENV: `PROXY_SERVER_NAME`) directive and the `CN` field in the SSL certificate have been both set to 'localhost'. This should obviously not be used for production.
|
||||||
|
|
||||||
The proxy locations, ports and other NGINX options can be modified in the `.env` file:
|
The proxy locations, ports and other NGINX options can be modified in the `.env` file:
|
||||||
|
|
@ -359,17 +359,18 @@ NGINX_SSLPORT=443
|
||||||
NGINX_LOG_DIR=/var/log/nginx
|
NGINX_LOG_DIR=/var/log/nginx
|
||||||
|
|
||||||
# Check CKAN__ROOT_PATH and CKANEXT__DCAT__BASE_URI. If you don't need to use domain locations, it is better to use the nginx configuration. Leave blank or use the root `/`.
|
# Check CKAN__ROOT_PATH and CKANEXT__DCAT__BASE_URI. If you don't need to use domain locations, it is better to use the nginx configuration. Leave blank or use the root `/`.
|
||||||
PROXY_SERVER_NAME=192.168.68.106
|
PROXY_SERVER_NAME=localhost
|
||||||
PROXY_CKAN_LOCATION=/catalog
|
PROXY_CKAN_LOCATION=/catalog
|
||||||
PROXY_PYCSW_LOCATION=/csw
|
PROXY_PYCSW_LOCATION=/csw
|
||||||
```
|
```
|
||||||
|
The base Docker Compose configuration uses an NGINX image as the front-end (ie: reverse proxy). It includes HTTPS running on port number 8443. A "self-signed" SSL certificate is generated as part of the ENTRYPOINT. The ENV `PROXY_SERVER_NAME`, NGINX `server_name` directive and the `CN` field in the SSL certificate have been both set to 'localhost'. This should obviously not be used for production.
|
||||||
|
|
||||||
Creating the SSL cert and key files as follows:
|
Creating the SSL cert and key files as follows:
|
||||||
`openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 -subj "/C=DE/ST=Berlin/L=Berlin/O=None/CN=localhost" -keyout ckan-local.key -out ckan-local.crt`
|
`openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 -subj "/C=DE/ST=Berlin/L=Berlin/O=None/CN=localhost" -keyout ckan-local.key -out ckan-local.crt`
|
||||||
The `ckan-local.*` files will then need to be moved into the nginx/setup/ directory
|
The `ckan-local.*` files will then need to be moved into the nginx/setup/ directory
|
||||||
|
|
||||||
|
|
||||||
### Apache HTTP Server
|
#### Apache HTTP Server
|
||||||
The Docker Compose configuration ([`docker-compose.apache.yml`](/docker-compose.apache.yml)) uses an httpd image as the front-end. It has two routes for the ckan (default location: `/catalog`) and ckan-pycsw (default location: `/csw`) services.
|
The Docker Compose configuration ([`docker-compose.apache.yml`](/docker-compose.apache.yml)) uses an httpd image as the front-end. It has two routes for the ckan (default location: `/catalog`) and ckan-pycsw (default location: `/csw`) services.
|
||||||
|
|
||||||
The proxy locations, ports and other Apache Web Server options can be modified in the `.env` file:
|
The proxy locations, ports and other Apache Web Server options can be modified in the `.env` file:
|
||||||
|
|
@ -383,7 +384,7 @@ APACHE_PORT=80
|
||||||
APACHE_LOG_DIR=/var/log/apache
|
APACHE_LOG_DIR=/var/log/apache
|
||||||
|
|
||||||
# Check CKAN__ROOT_PATH and CKANEXT__DCAT__BASE_URI. If you don't need to use domain locations, it is better to use the nginx configuration. Leave blank or use the root `/`.
|
# Check CKAN__ROOT_PATH and CKANEXT__DCAT__BASE_URI. If you don't need to use domain locations, it is better to use the nginx configuration. Leave blank or use the root `/`.
|
||||||
PROXY_SERVER_NAME=192.168.68.106
|
PROXY_SERVER_NAME=localhost
|
||||||
PROXY_CKAN_LOCATION=/catalog
|
PROXY_CKAN_LOCATION=/catalog
|
||||||
PROXY_PYCSW_LOCATION=/csw
|
PROXY_PYCSW_LOCATION=/csw
|
||||||
```
|
```
|
||||||
|
|
@ -409,9 +410,15 @@ These parameters can be added to the `.env` file
|
||||||
|
|
||||||
For more information please see [ckanext-envvars](https://github.com/okfn/ckanext-envvars)
|
For more information please see [ckanext-envvars](https://github.com/okfn/ckanext-envvars)
|
||||||
|
|
||||||
## xloader
|
|
||||||
|
### Datastore
|
||||||
|
The Datastore database and user is created as part of the entrypoint scripts for the db container.
|
||||||
|
|
||||||
|
|
||||||
|
### xloader
|
||||||
To replacing DataPusher with XLoader check out the wiki page for this: https://github.com/ckan/ckan-docker/wiki/Replacing-DataPusher-with-XLoader
|
To replacing DataPusher with XLoader check out the wiki page for this: https://github.com/ckan/ckan-docker/wiki/Replacing-DataPusher-with-XLoader
|
||||||
|
|
||||||
|
|
||||||
### ckan-pycsw
|
### ckan-pycsw
|
||||||
[ckan-pycsw](https://github.com/mjanez/ckan-pycsw) is a docker compose environment (based on [pycsw](https://github.com/geopython/pycsw)) for development and testing with CKAN Open Data portals.[^5]
|
[ckan-pycsw](https://github.com/mjanez/ckan-pycsw) is a docker compose environment (based on [pycsw](https://github.com/geopython/pycsw)) for development and testing with CKAN Open Data portals.[^5]
|
||||||
|
|
||||||
|
|
@ -419,11 +426,13 @@ Available components:
|
||||||
* **pycsw**: The pycsw app. An [OARec](https://ogcapi.ogc.org/records) and [OGC CSW](https://opengeospatial.org/standards/cat) server implementation written in Python.
|
* **pycsw**: The pycsw app. An [OARec](https://ogcapi.ogc.org/records) and [OGC CSW](https://opengeospatial.org/standards/cat) server implementation written in Python.
|
||||||
* **ckan2pycsw**: Software to achieve interoperability with the open data portals based on CKAN. To do this, ckan2pycsw reads data from an instance using the CKAN API, generates ISO-19115/ISO-19139 metadata using [pygeometa](https://geopython.github.io/pygeometa/), or a custom schema that is based on a customized CKAN schema, and populates a [pycsw](https://pycsw.org/) instance that exposes the metadata using CSW and OAI-PMH.
|
* **ckan2pycsw**: Software to achieve interoperability with the open data portals based on CKAN. To do this, ckan2pycsw reads data from an instance using the CKAN API, generates ISO-19115/ISO-19139 metadata using [pygeometa](https://geopython.github.io/pygeometa/), or a custom schema that is based on a customized CKAN schema, and populates a [pycsw](https://pycsw.org/) instance that exposes the metadata using CSW and OAI-PMH.
|
||||||
|
|
||||||
|
|
||||||
## ckan-docker tips
|
## ckan-docker tips
|
||||||
### CKAN. Backups
|
### CKAN. Backups
|
||||||
PostgreSQL offers the command line tools [`pg_dump`](https://www.postgresql.org/docs/current/static/app-pgdump.html) and [`pg_restore`](https://www.postgresql.org/docs/current/static/app-pgrestore.html) for dumping and restoring a database and its content to/from a file.
|
PostgreSQL offers the command line tools [`pg_dump`](https://www.postgresql.org/docs/current/static/app-pgdump.html) and [`pg_restore`](https://www.postgresql.org/docs/current/static/app-pgrestore.html) for dumping and restoring a database and its content to/from a file.
|
||||||
|
|
||||||
### Backup service for db container
|
|
||||||
|
#### Backup service for db container
|
||||||
1. Create a new file called `ckan_backup_custom.sh` and open it in your preferred text editor.
|
1. Create a new file called `ckan_backup_custom.sh` and open it in your preferred text editor.
|
||||||
|
|
||||||
2. Add the following code to the script, replacing the placeholders with your actual values:
|
2. Add the following code to the script, replacing the placeholders with your actual values:
|
||||||
|
|
@ -480,7 +489,8 @@ The cronjob is now set up and will backup your CKAN PostgreSQL database daily at
|
||||||
>**Info**<br>
|
>**Info**<br>
|
||||||
> Sample scripts for backing up CKAN: [`doc/scripts`](doc/scripts)
|
> Sample scripts for backing up CKAN: [`doc/scripts`](doc/scripts)
|
||||||
|
|
||||||
### Restore a backup
|
|
||||||
|
#### Restore a backup
|
||||||
If need to use a backup, restore it:
|
If need to use a backup, restore it:
|
||||||
|
|
||||||
1. First clean the database. **Caution, this will delete all data from your CKAN database!**
|
1. First clean the database. **Caution, this will delete all data from your CKAN database!**
|
||||||
|
|
@ -498,6 +508,33 @@ If need to use a backup, restore it:
|
||||||
docker exec -e PGPASSWORD=$POSTGRES_PASSWORD $POSTGRESQL_CONTAINER_NAME pg_restore -U $POSTGRES_USER --clean --if-exists -d $DATABASE_NAME < /path/to/your/backup/directory/ckan.dump
|
docker exec -e PGPASSWORD=$POSTGRES_PASSWORD $POSTGRESQL_CONTAINER_NAME pg_restore -U $POSTGRES_USER --clean --if-exists -d $DATABASE_NAME < /path/to/your/backup/directory/ckan.dump
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
### CKAN. Manage new users
|
||||||
|
|
||||||
|
1. Create a new user from the Docker host, for example to create a new user called 'admin'
|
||||||
|
|
||||||
|
```bash
|
||||||
|
docker exec -it <container-id> ckan -c ckan.ini user add admin email=admin@localhost
|
||||||
|
```
|
||||||
|
|
||||||
|
To delete the 'admin' user
|
||||||
|
|
||||||
|
```bash
|
||||||
|
docker exec -it <container-id> ckan -c ckan.ini user remove admin`
|
||||||
|
```
|
||||||
|
|
||||||
|
1. Create a new user from within the ckan container. You will need to get a session on the running container
|
||||||
|
|
||||||
|
```bash
|
||||||
|
ckan -c ckan.ini user add admin email=admin@localhost`
|
||||||
|
```
|
||||||
|
|
||||||
|
To delete the 'admin' user
|
||||||
|
```bash
|
||||||
|
ckan -c ckan.ini user remove admin`
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
### Docker. Basic commands
|
### Docker. Basic commands
|
||||||
#### Linux post-install steps
|
#### Linux post-install steps
|
||||||
[These optional post-installation procedures](https://docs.docker.com/engine/install/linux-postinstall/) shows you how to configure your Linux host machine to work better with Docker. For example, managing docker with [a non-root user](https://docs.docker.com/engine/install/linux-postinstall/#manage-docker-as-a-non-root-user).
|
[These optional post-installation procedures](https://docs.docker.com/engine/install/linux-postinstall/) shows you how to configure your Linux host machine to work better with Docker. For example, managing docker with [a non-root user](https://docs.docker.com/engine/install/linux-postinstall/#manage-docker-as-a-non-root-user).
|
||||||
|
|
@ -510,6 +547,7 @@ sudo systemctl enable docker
|
||||||
sudo systemctl disable docker
|
sudo systemctl disable docker
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
#### Clear all Docker unused objects (images, containers, networks, local volumes)
|
#### Clear all Docker unused objects (images, containers, networks, local volumes)
|
||||||
```bash
|
```bash
|
||||||
docker system prune # Clear all
|
docker system prune # Clear all
|
||||||
|
|
@ -520,6 +558,7 @@ docker volume prune # Clear unused volumes
|
||||||
docker network prune # Clear unused networks
|
docker network prune # Clear unused networks
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Docker Compose. Basic commands
|
### Docker Compose. Basic commands
|
||||||
More info about Docker Compose commands at [docker compose reference](https://docs.docker.com/compose/reference/).
|
More info about Docker Compose commands at [docker compose reference](https://docs.docker.com/compose/reference/).
|
||||||
|
|
||||||
|
|
@ -569,6 +608,7 @@ docker compose [-f <docker compose-file>] -p <my_project> up -d --build
|
||||||
docker compose [-p <my_project>] down
|
docker compose [-p <my_project>] down
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
### Docker Compose. Configure a docker compose service to start on boot
|
### Docker Compose. Configure a docker compose service to start on boot
|
||||||
To have Docker Compose run automatically when you reboot a machine, you can follow the steps below:
|
To have Docker Compose run automatically when you reboot a machine, you can follow the steps below:
|
||||||
1. Create a systemd service file for Docker Compose. You can create a file named `ckan-docker-compose.service` in the `/etc/systemd/system/` folder with the following content:
|
1. Create a systemd service file for Docker Compose. You can create a file named `ckan-docker-compose.service` in the `/etc/systemd/system/` folder with the following content:
|
||||||
|
|
|
||||||
|
|
@ -74,23 +74,21 @@ services:
|
||||||
container_name: ${POSTGRESQL_CONTAINER_NAME}
|
container_name: ${POSTGRESQL_CONTAINER_NAME}
|
||||||
build:
|
build:
|
||||||
context: postgresql/
|
context: postgresql/
|
||||||
args:
|
|
||||||
- DATASTORE_READONLY_PASSWORD=${DATASTORE_READONLY_PASSWORD}
|
|
||||||
- POSTGRES_PASSWORD=${POSTGRES_PASSWORD}
|
|
||||||
environment:
|
environment:
|
||||||
- DATASTORE_READONLY_PASSWORD=${DATASTORE_READONLY_PASSWORD}
|
- POSTGRES_USER
|
||||||
- POSTGRES_PASSWORD=${POSTGRES_PASSWORD}
|
- POSTGRES_PASSWORD
|
||||||
- PGDATA=/var/lib/postgresql/data/db
|
- POSTGRES_DB
|
||||||
logging:
|
- CKAN_DB_USER
|
||||||
driver: "json-file"
|
- CKAN_DB_PASSWORD
|
||||||
options:
|
- CKAN_DB
|
||||||
max-size: "100m"
|
- DATASTORE_READONLY_USER
|
||||||
max-file: "10"
|
- DATASTORE_READONLY_PASSWORD
|
||||||
|
- DATASTORE_DB
|
||||||
volumes:
|
volumes:
|
||||||
- pg_data:/var/lib/postgresql/data
|
- pg_data:/var/lib/postgresql/data
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
healthcheck:
|
healthcheck:
|
||||||
test: ["CMD", "pg_isready", "-U", "ckan"]
|
test: ["CMD", "pg_isready", "-U", "${POSTGRES_USER}", "-d", "${POSTGRES_DB}"]
|
||||||
|
|
||||||
solr:
|
solr:
|
||||||
container_name: ${SOLR_CONTAINER_NAME}
|
container_name: ${SOLR_CONTAINER_NAME}
|
||||||
|
|
@ -112,9 +110,6 @@ services:
|
||||||
|
|
||||||
redis:
|
redis:
|
||||||
container_name: ${REDIS_CONTAINER_NAME}
|
container_name: ${REDIS_CONTAINER_NAME}
|
||||||
# build:
|
|
||||||
# context: redis/
|
|
||||||
# dockerfile: Dockerfile
|
|
||||||
image: redis:${REDIS_VERSION}
|
image: redis:${REDIS_VERSION}
|
||||||
logging:
|
logging:
|
||||||
driver: "json-file"
|
driver: "json-file"
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,6 @@
|
||||||
version: "3"
|
version: "3"
|
||||||
|
|
||||||
|
|
||||||
volumes:
|
volumes:
|
||||||
ckan_storage:
|
ckan_storage:
|
||||||
pg_data:
|
pg_data:
|
||||||
|
|
@ -18,11 +19,13 @@ services:
|
||||||
options:
|
options:
|
||||||
max-size: "100m"
|
max-size: "100m"
|
||||||
max-file: "10"
|
max-file: "10"
|
||||||
|
networks:
|
||||||
|
- webnet
|
||||||
|
- ckannet
|
||||||
depends_on:
|
depends_on:
|
||||||
ckan:
|
ckan:
|
||||||
condition: service_healthy
|
condition: service_healthy
|
||||||
ports:
|
ports:
|
||||||
- "0.0.0.0:${NGINX_PORT_HOST}:${NGINX_PORT}"
|
|
||||||
- "0.0.0.0:${NGINX_SSLPORT_HOST}:${NGINX_SSLPORT}"
|
- "0.0.0.0:${NGINX_SSLPORT_HOST}:${NGINX_SSLPORT}"
|
||||||
|
|
||||||
ckan:
|
ckan:
|
||||||
|
|
@ -30,6 +33,13 @@ services:
|
||||||
build:
|
build:
|
||||||
context: ckan/
|
context: ckan/
|
||||||
dockerfile: Dockerfile
|
dockerfile: Dockerfile
|
||||||
|
args:
|
||||||
|
- TZ=${TZ}
|
||||||
|
networks:
|
||||||
|
- ckannet
|
||||||
|
- dbnet
|
||||||
|
- solrnet
|
||||||
|
- redisnet
|
||||||
env_file:
|
env_file:
|
||||||
- .env
|
- .env
|
||||||
logging:
|
logging:
|
||||||
|
|
@ -44,8 +54,6 @@ services:
|
||||||
condition: service_healthy
|
condition: service_healthy
|
||||||
redis:
|
redis:
|
||||||
condition: service_healthy
|
condition: service_healthy
|
||||||
ports:
|
|
||||||
- "0.0.0.0:${CKAN_PORT_HOST}:${CKAN_PORT}"
|
|
||||||
volumes:
|
volumes:
|
||||||
- ckan_storage:/var/lib/ckan
|
- ckan_storage:/var/lib/ckan
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
|
|
@ -64,6 +72,9 @@ services:
|
||||||
options:
|
options:
|
||||||
max-size: "100m"
|
max-size: "100m"
|
||||||
max-file: "10"
|
max-file: "10"
|
||||||
|
networks:
|
||||||
|
- webnet
|
||||||
|
- ckannet
|
||||||
depends_on:
|
depends_on:
|
||||||
ckan:
|
ckan:
|
||||||
condition: service_healthy
|
condition: service_healthy
|
||||||
|
|
@ -80,13 +91,18 @@ services:
|
||||||
container_name: ${POSTGRESQL_CONTAINER_NAME}
|
container_name: ${POSTGRESQL_CONTAINER_NAME}
|
||||||
build:
|
build:
|
||||||
context: postgresql/
|
context: postgresql/
|
||||||
args:
|
networks:
|
||||||
- DATASTORE_READONLY_PASSWORD=${DATASTORE_READONLY_PASSWORD}
|
- dbnet
|
||||||
- POSTGRES_PASSWORD=${POSTGRES_PASSWORD}
|
|
||||||
environment:
|
environment:
|
||||||
- DATASTORE_READONLY_PASSWORD=${DATASTORE_READONLY_PASSWORD}
|
- POSTGRES_USER
|
||||||
- POSTGRES_PASSWORD=${POSTGRES_PASSWORD}
|
- POSTGRES_PASSWORD
|
||||||
- PGDATA=/var/lib/postgresql/data/db
|
- POSTGRES_DB
|
||||||
|
- CKAN_DB_USER
|
||||||
|
- CKAN_DB_PASSWORD
|
||||||
|
- CKAN_DB
|
||||||
|
- DATASTORE_READONLY_USER
|
||||||
|
- DATASTORE_READONLY_PASSWORD
|
||||||
|
- DATASTORE_DB
|
||||||
volumes:
|
volumes:
|
||||||
- pg_data:/var/lib/postgresql/data
|
- pg_data:/var/lib/postgresql/data
|
||||||
logging:
|
logging:
|
||||||
|
|
@ -96,13 +112,15 @@ services:
|
||||||
max-file: "10"
|
max-file: "10"
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
healthcheck:
|
healthcheck:
|
||||||
test: ["CMD", "pg_isready", "-U", "ckan"]
|
test: ["CMD", "pg_isready", "-U", "${POSTGRES_USER}", "-d", "${POSTGRES_DB}"]
|
||||||
|
|
||||||
solr:
|
solr:
|
||||||
container_name: ${SOLR_CONTAINER_NAME}
|
container_name: ${SOLR_CONTAINER_NAME}
|
||||||
build:
|
build:
|
||||||
context: solr/
|
context: solr/
|
||||||
dockerfile: Dockerfile.spatial
|
dockerfile: Dockerfile.spatial
|
||||||
|
networks:
|
||||||
|
- solrnet
|
||||||
image: ckan/ckan-solr:${SOLR_IMAGE_VERSION}
|
image: ckan/ckan-solr:${SOLR_IMAGE_VERSION}
|
||||||
env_file:
|
env_file:
|
||||||
- .env
|
- .env
|
||||||
|
|
@ -125,6 +143,18 @@ services:
|
||||||
options:
|
options:
|
||||||
max-size: "100m"
|
max-size: "100m"
|
||||||
max-file: "10"
|
max-file: "10"
|
||||||
|
networks:
|
||||||
|
- redisnet
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
healthcheck:
|
healthcheck:
|
||||||
test: ["CMD", "redis-cli", "-e", "QUIT"]
|
test: ["CMD", "redis-cli", "-e", "QUIT"]
|
||||||
|
|
||||||
|
networks:
|
||||||
|
webnet:
|
||||||
|
ckannet:
|
||||||
|
solrnet:
|
||||||
|
internal: true
|
||||||
|
dbnet:
|
||||||
|
internal: true
|
||||||
|
redisnet:
|
||||||
|
internal: true
|
||||||
|
|
|
||||||
|
|
@ -14,13 +14,22 @@ ENV NGINX_PORT=80
|
||||||
ENV NGINX_LOG_DIR=/var/log/nginx
|
ENV NGINX_LOG_DIR=/var/log/nginx
|
||||||
ENV NGINX_DIR=/etc/nginx
|
ENV NGINX_DIR=/etc/nginx
|
||||||
|
|
||||||
RUN mkdir -p ${NGINX_LOG_DIR}
|
RUN mkdir -p ${NGINX_LOG_DIR} && \
|
||||||
|
mkdir -p ${NGINX_DIR}/certs && \
|
||||||
|
apk update --no-cache && \
|
||||||
|
apk upgrade --no-cache && \
|
||||||
|
apk add --no-cache openssl
|
||||||
|
|
||||||
COPY setup/nginx.conf ${NGINX_DIR}/nginx.conf
|
COPY setup/nginx.conf ${NGINX_DIR}/nginx.conf
|
||||||
COPY setup/index.html /usr/share/nginx/html/index.html
|
COPY setup/index.html /usr/share/nginx/html/index.html
|
||||||
COPY setup/default.conf.template ${NGINX_DIR}/templates/default.conf.template
|
COPY setup/default.conf.template ${NGINX_DIR}/templates/default.conf.template
|
||||||
|
|
||||||
RUN mkdir -p ${NGINX_DIR}/certs
|
ENTRYPOINT \
|
||||||
COPY setup/ckan-local.* ${NGINX_DIR}/certs/
|
openssl req \
|
||||||
|
-subj '/C=DE/ST=Berlin/L=Berlin/O=None/CN=${PROXY_SERVER_NAME}' \
|
||||||
EXPOSE ${NGINX_PORT}
|
-x509 -newkey rsa:4096 \
|
||||||
|
-nodes -keyout /etc/nginx/ssl/default_key.pem \
|
||||||
|
-keyout ${NGINX_DIR}/certs/ckan-local.key \
|
||||||
|
-out ${NGINX_DIR}/certs/ckan-local.crt \
|
||||||
|
-days 365 && \
|
||||||
|
nginx -g 'daemon off;'
|
||||||
|
|
@ -7,6 +7,18 @@ server {
|
||||||
ssl_certificate /etc/nginx/certs/ckan-local.crt;
|
ssl_certificate /etc/nginx/certs/ckan-local.crt;
|
||||||
ssl_certificate_key /etc/nginx/certs/ckan-local.key;
|
ssl_certificate_key /etc/nginx/certs/ckan-local.key;
|
||||||
|
|
||||||
|
# TLS 1.2 & 1.3 only
|
||||||
|
ssl_protocols TLSv1.2 TLSv1.3;
|
||||||
|
|
||||||
|
# Disable weak ciphers
|
||||||
|
ssl_prefer_server_ciphers on;
|
||||||
|
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
|
||||||
|
|
||||||
|
# SSL sessions
|
||||||
|
ssl_session_timeout 1d;
|
||||||
|
# ssl_session_cache dfine in stream and http
|
||||||
|
ssl_session_tickets off;
|
||||||
|
|
||||||
#access_log /var/log/nginx/host.access.log main;
|
#access_log /var/log/nginx/host.access.log main;
|
||||||
|
|
||||||
location ${PROXY_CKAN_LOCATION} {
|
location ${PROXY_CKAN_LOCATION} {
|
||||||
|
|
@ -29,12 +41,14 @@ server {
|
||||||
proxy_cache_key $host$scheme$proxy_host$request_uri;
|
proxy_cache_key $host$scheme$proxy_host$request_uri;
|
||||||
}
|
}
|
||||||
|
|
||||||
error_page 404 /404.html;
|
error_page 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 421 422 423 424 425 426 428 429 431 451 500 501 502 503 504 505 506 507 508 510 511 /error.html;
|
||||||
|
|
||||||
# redirect server error pages to the static page /50x.html
|
# redirect server error pages to the static page /error.html
|
||||||
#
|
#
|
||||||
error_page 500 502 503 504 /50x.html;
|
location = /error.html {
|
||||||
location = /50x.html {
|
ssi on;
|
||||||
|
internal;
|
||||||
|
auth_basic off;
|
||||||
root /usr/share/nginx/html;
|
root /usr/share/nginx/html;
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -22,14 +22,70 @@ http {
|
||||||
access_log /var/log/nginx/access.log main;
|
access_log /var/log/nginx/access.log main;
|
||||||
|
|
||||||
sendfile on;
|
sendfile on;
|
||||||
#tcp_nopush on;
|
tcp_nopush on;
|
||||||
|
tcp_nodelay on;
|
||||||
|
types_hash_max_size 2048;
|
||||||
keepalive_timeout 65;
|
keepalive_timeout 65;
|
||||||
|
|
||||||
#gzip on;
|
# Don't expose Nginx version
|
||||||
|
server_tokens off;
|
||||||
|
|
||||||
|
# Prevent clickjacking attacks
|
||||||
|
add_header X-Frame-Options "SAMEORIGIN";
|
||||||
|
|
||||||
|
# Mitigate Cross-Site scripting attack
|
||||||
|
add_header X-XSS-Protection "1; mode=block";
|
||||||
|
|
||||||
|
# Enable gzip encryption
|
||||||
|
gzip on;
|
||||||
|
|
||||||
proxy_cache_path /tmp/nginx_cache levels=1:2 keys_zone=cache:30m max_size=250m;
|
proxy_cache_path /tmp/nginx_cache levels=1:2 keys_zone=cache:30m max_size=250m;
|
||||||
proxy_temp_path /tmp/nginx_proxy 1 2;
|
proxy_temp_path /tmp/nginx_proxy 1 2;
|
||||||
|
|
||||||
include /etc/nginx/conf.d/*.conf;
|
include /etc/nginx/conf.d/*.conf;
|
||||||
|
|
||||||
|
# Error status text
|
||||||
|
map $status $status_text {
|
||||||
|
400 'Bad Request';
|
||||||
|
401 'Unauthorized';
|
||||||
|
402 'Payment Required';
|
||||||
|
403 'Forbidden';
|
||||||
|
404 'Not Found';
|
||||||
|
405 'Method Not Allowed';
|
||||||
|
406 'Not Acceptable';
|
||||||
|
407 'Proxy Authentication Required';
|
||||||
|
408 'Request Timeout';
|
||||||
|
409 'Conflict';
|
||||||
|
410 'Gone';
|
||||||
|
411 'Length Required';
|
||||||
|
412 'Precondition Failed';
|
||||||
|
413 'Payload Too Large';
|
||||||
|
414 'URI Too Long';
|
||||||
|
415 'Unsupported Media Type';
|
||||||
|
416 'Range Not Satisfiable';
|
||||||
|
417 'Expectation Failed';
|
||||||
|
418 'I\'m a teapot';
|
||||||
|
421 'Misdirected Request';
|
||||||
|
422 'Unprocessable Entity';
|
||||||
|
423 'Locked';
|
||||||
|
424 'Failed Dependency';
|
||||||
|
425 'Too Early';
|
||||||
|
426 'Upgrade Required';
|
||||||
|
428 'Precondition Required';
|
||||||
|
429 'Too Many Requests';
|
||||||
|
431 'Request Header Fields Too Large';
|
||||||
|
451 'Unavailable For Legal Reasons';
|
||||||
|
500 'Internal Server Error';
|
||||||
|
501 'Not Implemented';
|
||||||
|
502 'Bad Gateway';
|
||||||
|
503 'Service Unavailable';
|
||||||
|
504 'Gateway Timeout';
|
||||||
|
505 'HTTP Version Not Supported';
|
||||||
|
506 'Variant Also Negotiates';
|
||||||
|
507 'Insufficient Storage';
|
||||||
|
508 'Loop Detected';
|
||||||
|
510 'Not Extended';
|
||||||
|
511 'Network Authentication Required';
|
||||||
|
default 'Something is wrong';
|
||||||
|
}
|
||||||
}
|
}
|
||||||
|
|
@ -1,13 +1,4 @@
|
||||||
FROM postgres:15-alpine
|
FROM postgres:15-alpine
|
||||||
|
|
||||||
# Allow connections; we don't map out any ports so only linked docker containers can connect
|
|
||||||
RUN echo "host all all 0.0.0.0/0 md5" >> /var/lib/postgresql/data/pg_hba.conf
|
|
||||||
|
|
||||||
# Customize default user/pass/db
|
|
||||||
ENV POSTGRES_DB ckan
|
|
||||||
ENV POSTGRES_USER ckan
|
|
||||||
ARG POSTGRES_PASSWORD
|
|
||||||
ARG DATASTORE_READONLY_PASSWORD
|
|
||||||
|
|
||||||
# Include extra setup scripts (eg datastore)
|
# Include extra setup scripts (eg datastore)
|
||||||
ADD docker-entrypoint-initdb.d /docker-entrypoint-initdb.d
|
ADD docker-entrypoint-initdb.d /docker-entrypoint-initdb.d
|
||||||
|
|
@ -0,0 +1,7 @@
|
||||||
|
#!/bin/bash
|
||||||
|
set -e
|
||||||
|
|
||||||
|
psql -v ON_ERROR_STOP=1 --username "$POSTGRES_USER" <<-EOSQL
|
||||||
|
CREATE ROLE "$CKAN_DB_USER" NOSUPERUSER CREATEDB CREATEROLE LOGIN PASSWORD '$CKAN_DB_PASSWORD';
|
||||||
|
CREATE DATABASE "$CKAN_DB" OWNER "$CKAN_DB_USER" ENCODING 'utf-8';
|
||||||
|
EOSQL
|
||||||
|
|
@ -1,4 +0,0 @@
|
||||||
\set datastore_ro_password '\'' `echo $DATASTORE_READONLY_PASSWORD` '\''
|
|
||||||
|
|
||||||
CREATE ROLE datastore_ro NOSUPERUSER NOCREATEDB NOCREATEROLE LOGIN PASSWORD :datastore_ro_password;
|
|
||||||
CREATE DATABASE datastore OWNER ckan ENCODING 'utf-8';
|
|
||||||
|
|
@ -0,0 +1,7 @@
|
||||||
|
#!/bin/bash
|
||||||
|
set -e
|
||||||
|
|
||||||
|
psql -v ON_ERROR_STOP=1 --username "$POSTGRES_USER" <<-EOSQL
|
||||||
|
CREATE ROLE "$DATASTORE_READONLY_USER" NOSUPERUSER NOCREATEDB NOCREATEROLE LOGIN PASSWORD '$DATASTORE_READONLY_PASSWORD';
|
||||||
|
CREATE DATABASE "$DATASTORE_DB" OWNER "$CKAN_DB_USER" ENCODING 'utf-8';
|
||||||
|
EOSQL
|
||||||
|
|
@ -1,2 +0,0 @@
|
||||||
CREATE DATABASE ckan_test OWNER ckan ENCODING 'utf-8';
|
|
||||||
CREATE DATABASE datastore_test OWNER ckan ENCODING 'utf-8';
|
|
||||||
|
|
@ -0,0 +1,7 @@
|
||||||
|
#!/bin/bash
|
||||||
|
set -e
|
||||||
|
|
||||||
|
psql -v ON_ERROR_STOP=1 --username "$POSTGRES_USER" <<-EOSQL
|
||||||
|
CREATE DATABASE ckan_test OWNER "$CKAN_DB_USER" ENCODING 'utf-8';
|
||||||
|
CREATE DATABASE datastore_test OWNER "$CKAN_DB_USER" ENCODING 'utf-8';
|
||||||
|
EOSQL
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
FROM solr:8
|
FROM solr:9
|
||||||
|
|
||||||
ENV SOLR_PORT=8983
|
ENV SOLR_PORT=8983
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
FROM solr:8
|
FROM solr:9
|
||||||
|
|
||||||
ENV SOLR_PORT=8983
|
ENV SOLR_PORT=8983
|
||||||
|
|
||||||
|
|
|
||||||
Loading…
Reference in New Issue